While browsing my daily security news, I recently stumbled upon an intriguing article from Dark Reading titled “GenAI Writes Malicious Code to Spread AsyncRAT.” This piece sheds light on a concerning trend: cyber criminals use Generative Artificial Intelligence (GenAI) to create and distribute malware, specifically AsyncRAT.
In this article, I covered the following:
- A comprehensive understanding of AsyncRAT
- The role of GenAI in cyberattacks
- Static analysis of an AsyncRAT variant (Hand on practice)
- Application of the MITRE ATT&CK framework
- Mitigation strategies individuals and businesses can employ to stay safe
Understanding AsyncRAT
AsyncRAT first appeared on GitHub in 2019 as an open-source tool developed by an individual known as “NYANxCAT.” Its versatility and customizable features quickly gained traction among cybercriminals, leading to widespread adoption in various malware campaigns. AsyncRAT is a remote access Trojan (RAT) designed to provide attackers with remote administrative access to a victim’s machine. Once infected, this malware can steal sensitive information, monitor user activity, deploy additional malicious tools, and manipulate files. Its capabilities include Keylogging, Screen Capturing, File Management, Credential Harvesting and Installing Additional Malware.
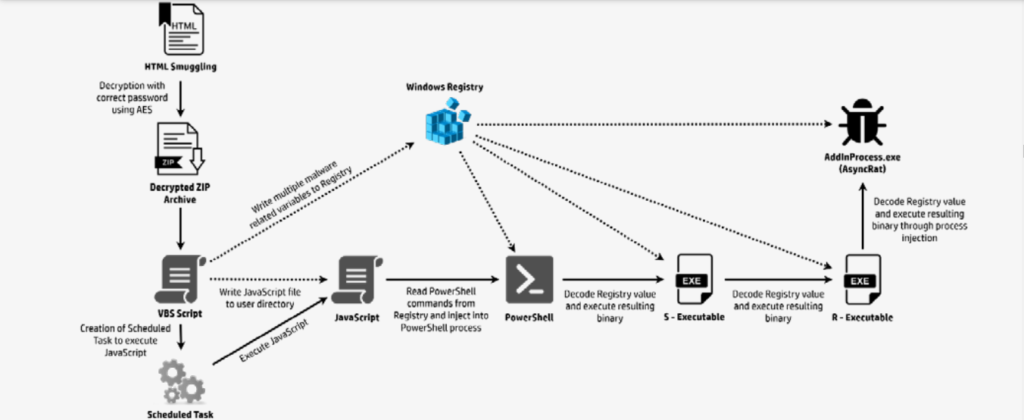
AsyncRAT is being used to target various sectors, including financial services, healthcare, retail and e-commerce, manufacturing, small to medium enterprises (SMEs), government, and education. The primary motivations for using AsyncRAT include stealing sensitive information for financial fraud or selling it on dark web marketplaces, ransom demands, and creating a network of compromised machines for DDoS attacks.
The Role of GenAI in Cyberattacks
Recent findings from HP Wolf Security highlighted a concerning trend where threat actors began leveraging GenAI to generate malware. This was exemplified in a phishing campaign where attackers utilised GenAI to write VBScript and JavaScript code to distribute AsyncRAT. In June 2024, researchers discovered a suspicious email containing a French invoice attachment that ultimately led them to the malicious code. The use of GenAI was evident through structured code, detailed comments, and function names indicating AI assistance. Unlike traditional malware, which is heavily obfuscated, this code was left unprotected, suggesting GenAI involvement.
The integration of GenAI in cybercrime lowers the technical barrier for attackers, enabling them to create sophisticated malware with less effort. However, while GenAI aids attackers, it can also serve as a tool for defenders to identify threats and patterns in malicious code.
Static Analysis of an AsyncRAT Variant: Hands-on practice
While watching Grant Collins’ video, I learned how cybersecurity professionals can analyse AsyncRAT malware through the following steps:
- Downloading the Source Code from GitHub.
- Deciding on Analysis Methods and tools to use.
- Static analysis methods which focus on examining what’s beneath the executable without running the program were selected. Tools used included VirusTotal, PEStudio, and Capa.
- Next, two virtual machines were created: Machine A, running Windows 10 with the Flare VM and necessary packages installed, and Machine B, serving as a C2 server running on REMnux, isolated from the internet using host-only adapter network settings.

Reading an article on Censys revealed that the AsyncRAT malware family contains a hardcoded TLS certificate. To track AsyncRAT malware using TLS certificates, I used censys.io by placing services.tls.certificates.leaf_data.subject.common_name:”AsyncRAT Server” in the search bar to see how many hosts are currently running the AsyncRAT server-side clients.
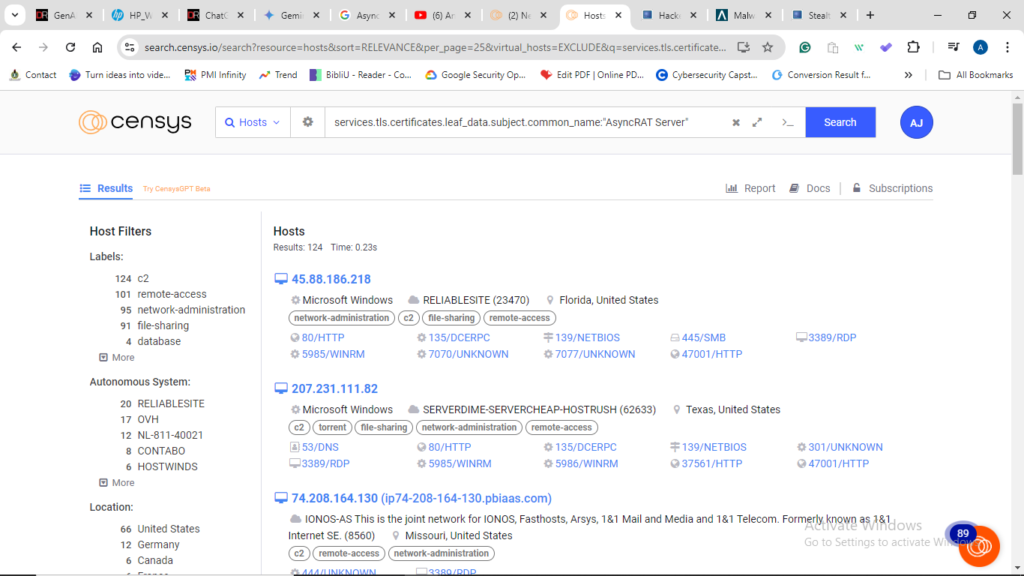
If the source code from GitHub were to be compiled, it would require the necessary binary files, and both a client and a server would need to be deployed. Alternatively, Malware Bazaar was used to download a variety of AsyncRAT samples in PDF format. This was done to gain insights into the contents of the AsyncRAT malware.
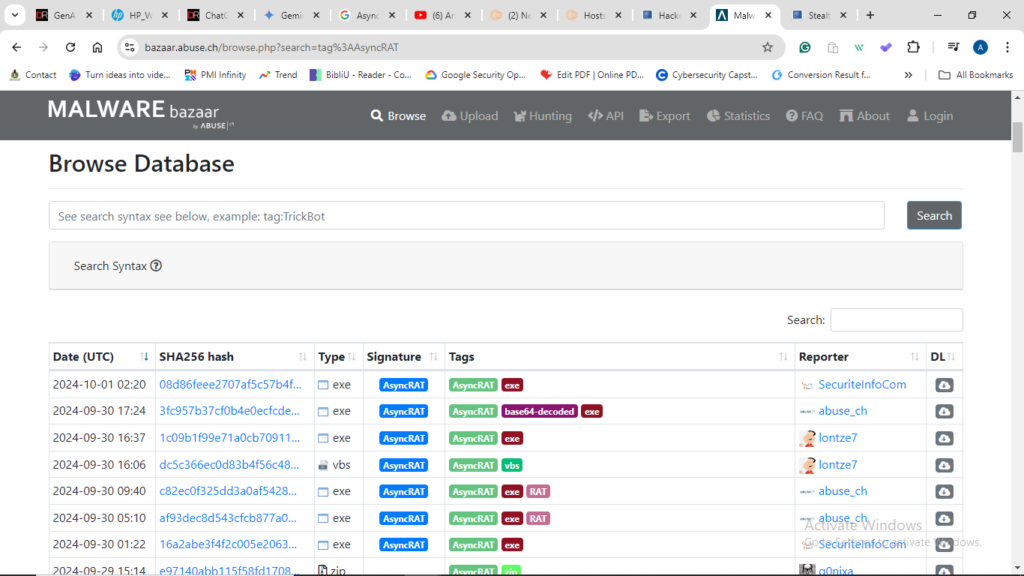
Preventive measure called defanging was taken when downloading malware from the repository. Defanging is a technique used in cybersecurity to render potentially dangerous or malicious content, safe for sharing or use without allowing them to be actively clickable or executable.
The Malware Bazaar platform does this by packaging files into an archived or compressed file format, such as .zip, and applying encryption as another preventive measure in case of accidental execution. Therefore, one must extract the files and enter the password to run the malware.
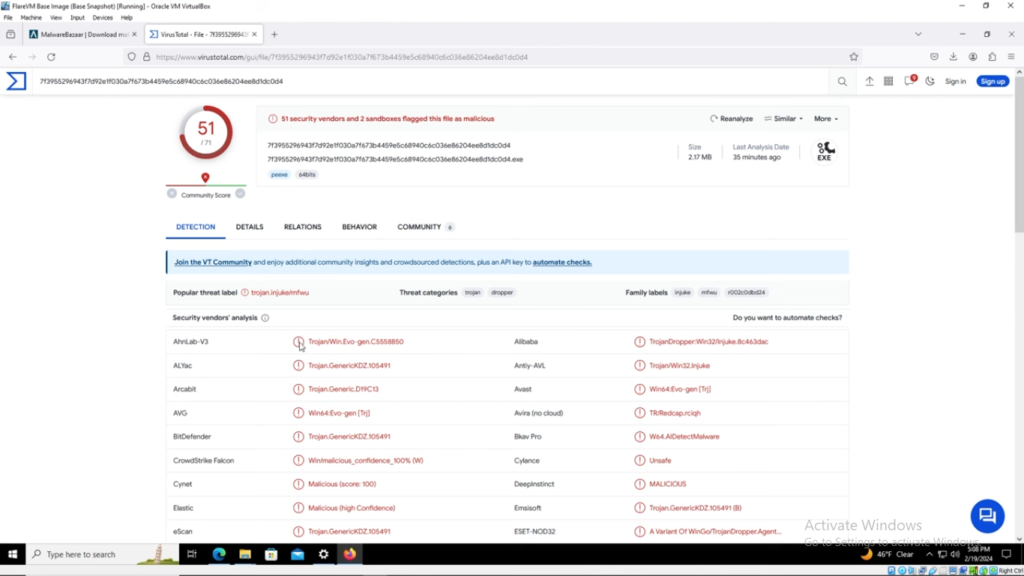
The malware was downloaded onto the Flare virtual machine. In the browser of that machine, VirusTotal was opened to analyse the malware by checking which common endpoint security engines flag the specific variant as malicious. Then, hashes were generated from the sample as a means of identification. This tool helped to identify the basic properties of the malware sample downloaded from Malware Bazaar.
Next, I opened the malware executable code in PEStudio to gather more details, such as strings, see the Windows API imports, and possibly identify if the malware is packed. This tool provided more clues about what is happening beneath the binary.
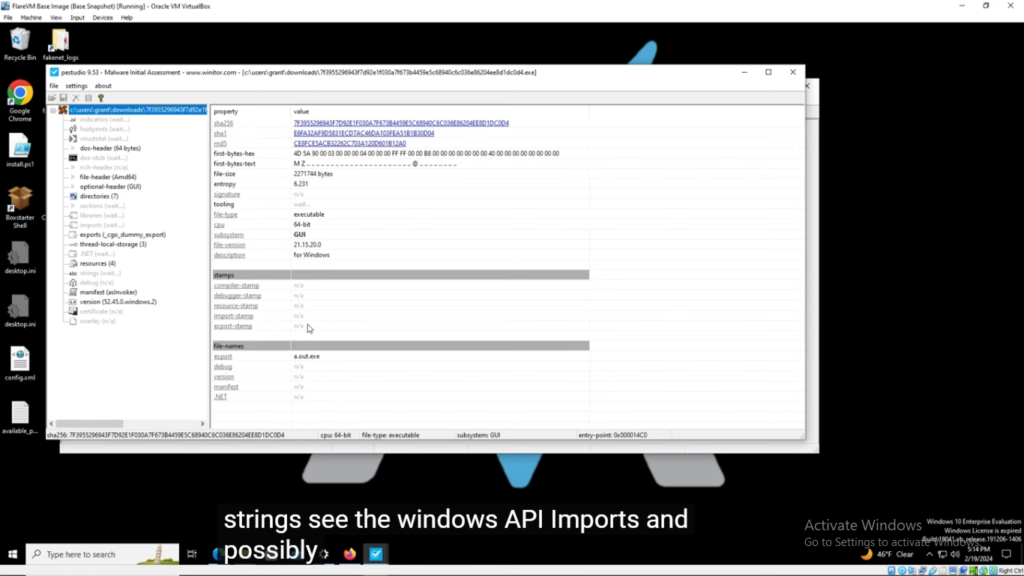
Analysis of the strings embedded within the program can reveal functionalities, and hardcoded values such as command control IP addresses, servers, and other interesting details.
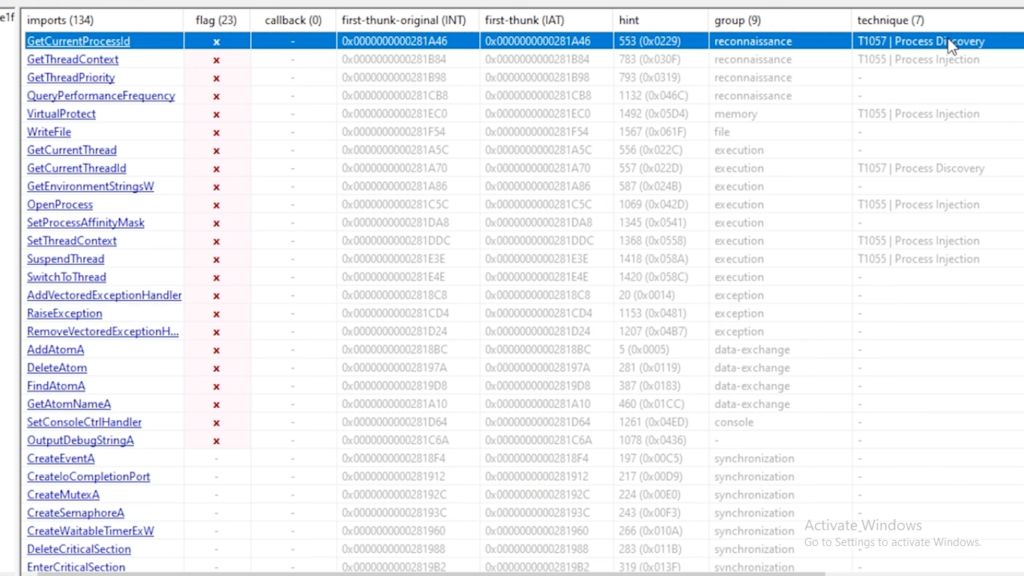
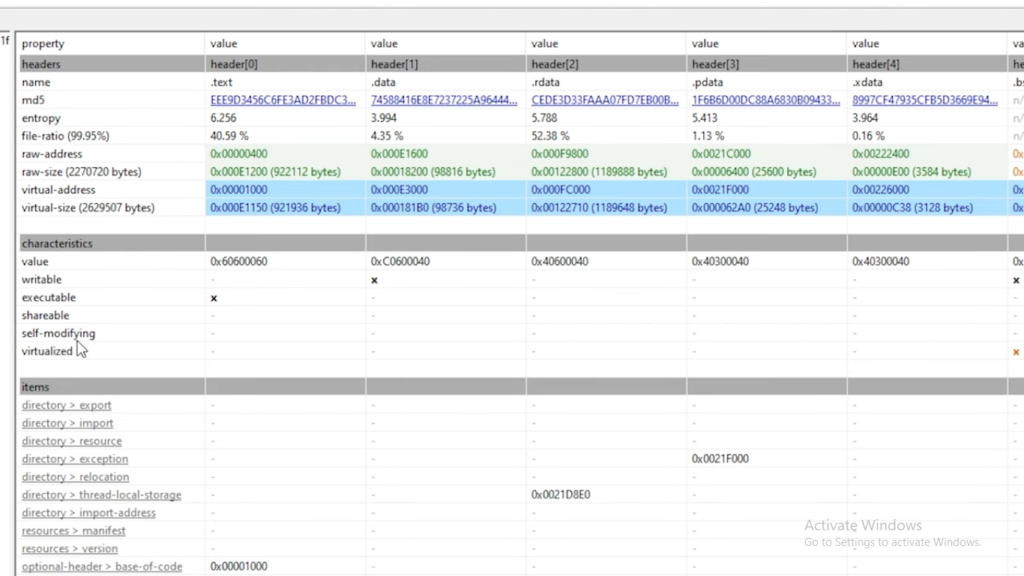
Outcome: Nothing unique was found, as most files had a .go extension indicating they were compiled in Go. However, the Windows API function imports show the general capabilities of the malware program. This flags an endpoint that can be used for process injection and writing files onto the file system. The analysis showed that the malware was not packed because the virtual versus raw sizes of the PE section headers were almost the same.
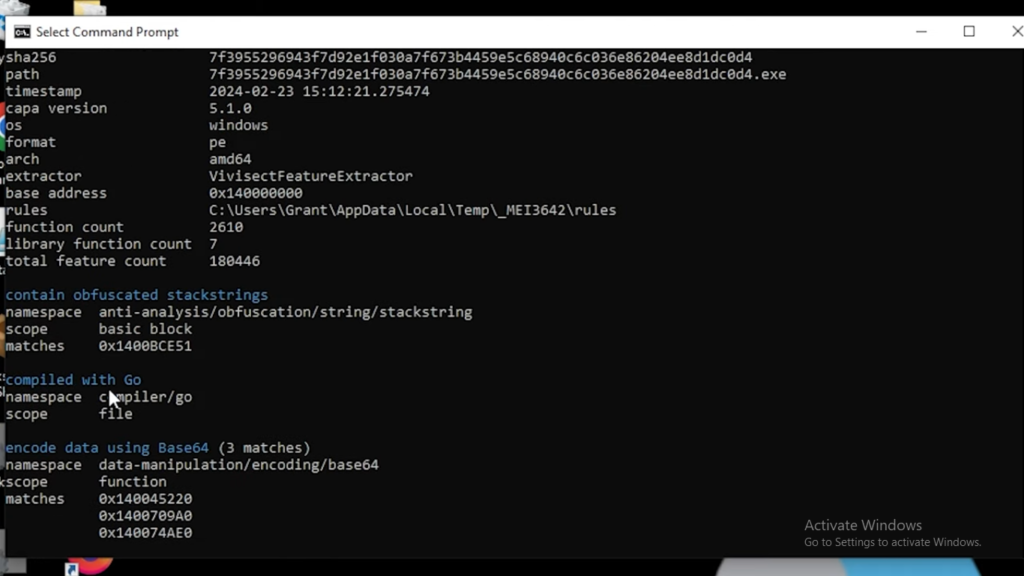
Capa, an open-source command-line interface (CLI) tool, was used to run the binary code to identify malicious behaviour and assess what is going on in the executable program. Same related behaviour as PEStudio was inferred.
Related: CVE-2024-28000 Vulnerability Exploit: Insights for WordPress Users
Utilising the MITRE ATT&CK Framework for AsyncRAT malware
The MITRE ATT&CK framework provides a structured approach to understanding how AsyncRAT operates. Mapping the tactics and techniques specific to AsyncRAT reveals its behaviours throughout the attack lifecycle, including:
1. Defence Evasion (TA0005)
- Debugger Evasion (T1622): AsyncRAT can use the CheckRemoteDebuggerPresent function to detect if it is being debugged, which helps it evade detection and analysis.
- Hide Artefacts: Hidden Window (T1564.003): AsyncRAT can hide the execution of scheduled tasks using ProcessWindowStyle.Hidden, preventing visible indicators of its presence.
- Virtualization/Sandbox Evasion: System Checks (T1497.001): AsyncRAT checks for strings like “Virtual,” “vmware,” or “VirtualBox” to determine if it’s running in a virtualized or sandbox environment, which helps it evade sandbox-based security solutions.
2. Command and Control (TA0011)
- Dynamic Resolution (T1568): AsyncRAT can be configured to use dynamic DNS (DDNS) to resolve its Command and Control (C2) infrastructure, allowing it to change its IP address while maintaining the same domain.
- Ingress Tool Transfer (T1105): AsyncRAT can download additional files over SFTP (Secure File Transfer Protocol) to enhance its attack capabilities or drop additional payloads.
3. Collection (TA0009)
- Input Capture: Keylogging (T1056.001): AsyncRAT can log keystrokes on the victim’s machine, allowing attackers to capture sensitive information such as usernames, passwords, and other input.
- Screen Capture (T1113): AsyncRAT can take screenshots of the victim’s screen to monitor user activity and exfiltrate sensitive data.
- Video Capture (T1125): AsyncRAT can record video or screen content, providing the attacker with live surveillance of the victim’s activity.
4. Discovery (TA0007)
- Process Discovery (T1057): AsyncRAT can examine running processes on the victim’s machine to detect debugging tools or other security software.
- System Information Discovery (T1082): AsyncRAT can gather information about the system, such as disk size and other system metrics, to determine the target’s environment.
- System Owner/User Discovery (T1033): AsyncRAT can identify whether the current user is an administrator, helping attackers determine if they have elevated privileges.
5. Execution (TA0002)
- Native API (T1106): AsyncRAT leverages operating system APIs, such as CheckRemoteDebuggerPresent, to interact with system functions and detect security mechanisms.
6. Persistence (TA0003)
- Scheduled Task/Job: Scheduled Task (T1053.005): AsyncRAT can create a scheduled task on the victim’s machine to maintain persistence across system reboots, ensuring that it executes on startup.
Recommended Mitigation Strategies for AsyncRAT
To defend against AsyncRAT, organisations should consider implementing the following strategies:
- Employ anti-debugging tools such as VMware ThinApp and behavioural analysis methods like Chronicle to detect malware trying to evade debuggers.
- Implement tools like Process Explorer to monitor hidden windows or tasks. Establish policies that prevent programs from launching with hidden window styles to enhance visibility.
- Use solutions such as Sandboxie to create a controlled environment that makes it difficult for malware to detect its execution context. Additionally, deploy detonation sandboxes like FireEye Malware Analysis that mimic physical environments for safe testing of suspicious files.
- Utilise tools like Cisco Umbrella or GCP Monitoring to monitor DNS traffic and detect anomalous domain lookups or dynamic DNS usage. Leverage threat intelligence platforms like Chronicle SIEM and SOAR to block known malicious dynamic DNS (DDNS) providers.
- Implement network monitoring tools such as Wireshark to detect suspicious file transfers. Employ Data Loss Prevention (DLP) solutions like Symantec DLP to prevent unauthorised file downloads.
- Use endpoint security tools such as Webroot SecureAnywhere to detect abnormal input capture behaviour. Regularly monitor for unusual process activity linked to keystroke logging.
- Implement behavioural monitoring tools like Cortex XDR to identify unauthorised applications attempting to capture the screen.
- Deploy security solutions such as Microsoft Defender for Endpoint that can detect unexpected video or screen recording events.
- Utilise tools like CrowdStrike Falcon to detect unauthorised process enumeration or discovery activities.
- Reduce the risk of information gathering by malicious actors by limiting user permissions using tools like Microsoft Active Directory or IAM systems to manage access controls effectively.
- Ensure user accounts have the necessary level of access using privilege management solutions.
- Use API monitoring tools such as Chronicle SIEM or Splunk to detect malicious or unauthorised API calls from applications like AsyncRAT.
- Regularly audit scheduled tasks using tools like Sysinternals Autoruns and implement endpoint detection tools like SentinelOne to detect suspicious or unauthorised task creation.
- Maintain up-to-date operating systems, software applications, and antivirus solutions, such as Norton or Kaspersky, by regularly applying security patches.
- Encourage vigilance regarding suspicious emails, attachments, and links by utilising email filtering tools like Proofpoint.
- Add an extra layer of security with multi-factor authentication (MFA) solutions like Authy or Duo Security to protect user accounts.
- Conduct training sessions using platforms like KnowBe4 to help employees recognize and avoid phishing scams effectively.
Conclusion
The rise of GenAI in cybercrime, particularly in the context of AsyncRAT, represents a significant shift in the threat landscape. Understanding how AsyncRAT operates and the techniques employed by cybercriminals is crucial for developing effective mitigation strategies. As technology continues to evolve, both attackers and defenders must adapt to stay ahead in the ongoing battle for cybersecurity.
By staying informed about emerging threats like AsyncRAT and leveraging tools like the MITRE ATT&CK framework, organisations can bolster their defences against these sophisticated cyber threats.
References
Aaron Jornet. (2023, September 20). AsyncRAT. MITRE ATT&CK.
https://attack.mitre.org/software/S1087/
Censys. (2024, February 9). A beginner’s guide to tracking malware infrastructure. https://censys.com/a-beginners-guide-to-tracking-malware-infrastructure/
Collins, G. (2024.). [Video]. YouTube. https://www.youtube.com/watch?v=2uCo_7-nYUA
HP WOLFSECURITY. (2024, September). Threat insights report. https://threatresearch.ext.hp.com/wp-content/uploads/2024/09/HP_Wolf_Security_Threat_In
sights_Report_September_2024.pdf
Montalbano, E. (2024, September 26). GenAI writes malicious code to spread AsyncRAT. Dark Reading. https://www.darkreading.com/cyber-risk/genai-writes-malicious-code-spread-asyncrat
Nelson, N. (2023, September 12). ChatGPT jailbreaking forums proliferate in dark web communities. Dark Reading.
https://www.darkreading.com/application-security/chatgpt-jailbreaking-forums-dark-web-communities
Toulas, B. (2024, January 7). Stealthy AsyncRAT malware attacks targets US infrastructure for 11 months. Bleeping Computer.
https://www.bleepingcomputer.com/news/security/stealthy-asyncrat-malware-attacks-targets-us-infrastructure-for-11-months/
What are MITRE ATT&CK techniques? (2024, April 11). Palo Alto Networks. https://www.paloaltonetworks.com/cyberpedia/what-are-mitre-attack-techniques#techniques
Abuse.ch. (n.d.). https://bazaar.abuse.ch/browse.php?search
Censys. (n.d.). https://search.censys.io/
VirusTotal. (n.d.). https://www.virustotal.com/




